Not everything online is what it seems. But then you already know that.
Spoofing, or copying, is a major source of online fraud. From website spoofing to software spoofing, pulling the digital wool over people’s eyes allows all kinds of sneaky activity to carry on.
In fact, device spoofing is one of the main methods used in many forms of digital fraud including ad fraud and click fraud.
So what can you do to avoid device spoofing affecting your online business?
First of all, let’s look at the basics.
What is device spoofing?
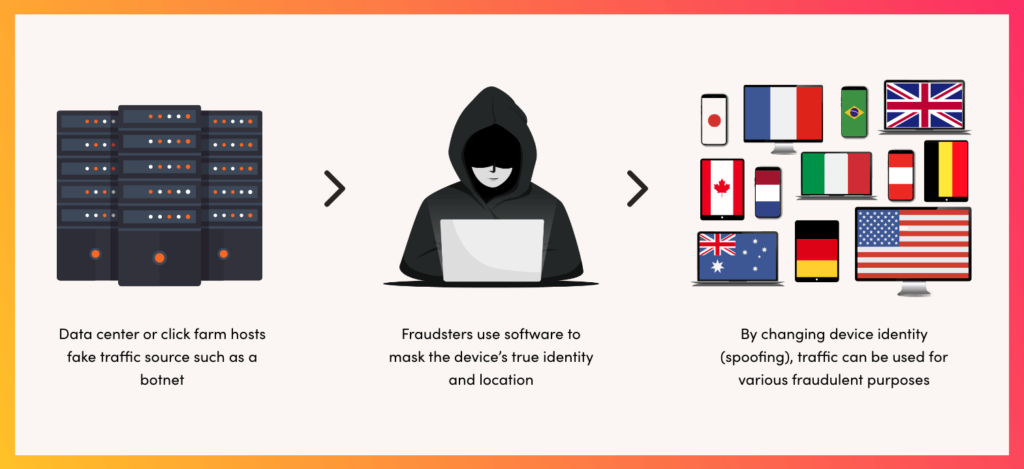
Device spoofing is the practice of presenting a digital device as something different, usually for fraudulent purposes, particularly ad fraud. For example, a server in a data center could change its device ID so that it appears to be a mobile device.
Device spoofing can use several processes including user agent spoofing, or UA spoofing. This is the process whereby the device presents a falsified user agent string, which is the unique identifier containing information about the device including:
- Operating system and version
- Processor and video card information
- Location information, often using IP address
- Device type including model
Presenting a false UA string is easily done using various developer tools, which are designed to help developers test software on different devices without changing their own device.
How is device spoofing used for fraud?
Using device spoofing for fraudulent purposes means that fraudsters can get around a number of security protocols. For example, many ad platforms or online services will use device fingerprinting as a way to identify who is using their services or visiting their websites.
Device fingerprinting uses several methods to identify the website visitor, using a mixture of the user agent string and also other techy processes such as the IP address, device hash, cookie hash and more.
Find out how device fingerprinting works.
This device fingerprinting can also be used to prevent certain types of device, browser or even specific locations from interacting with the online service. But if a fraudster can get around the device fingerprinting then they can conduct a variety of fraudulent or malicious activities.
This might include:
- Payment card fraud, also known as carding
- Advertising click fraud, also known as ad fraud
- Spam attacks, including the more serious spam SEO injection attack
- Malware injection
- Account takeover
Ad fraud is a growing problem, find out more in our blog
How do fraudsters make money with spoofed devices?
The most common reason for device spoofing is for ad fraud, which is the practice of generating fake traffic on paid ads.
This hugely lucrative industry makes fraudsters more money every year than credit card fraud, with an estimated $41 billion lost in 2021 to ad fraud. And for a very modest cost hackers can pick up readily available fingerprint spoofing software on the dark web.
Because ad fraud and click fraud are relatively simple criminal actions, with little in the way of repercussions, it has become a popular way for criminal networks to make some extra money.
In fact, there are even hobbyists making money with ad fraud by setting up simple click farms. By simply hiring a botnet based in a data center, ad fraudsters can run a basic campaign on a spoofed website and disappear.
And because device spoofing is a key part of this huge growing industry, this is one of the main reasons for its boom.
How common is device obfuscation in fraud?
Because many fraud attacks use bots and botnets, the common way to hide the traffic source is by using device spoofing. This allows bot traffic to visit a website or app while appearing to be a genuine human user.
Often, these bots will hide behind a VPN or proxy server, which allows them to switch IP addresses and present fake device information.
A VPN presents the easiest and most cost-effective way to dodge many security filters, which is one of the reasons why we pay close attention to VPN traffic here at ClickCease.
To be clear, just because a website visitor is using a VPN it doesn’t mean they are performing fraud. And in fact our filters will look at over 100 data points before blocking a user from clicking paid ads.
So, although not all VPN users are fraudulent, more often than not, fraudulent users are using VPNs.
So, how common are these spoofing or obfuscation methods?
Using fraud blocking on our own domain, we see:
- 41% of ad traffic blocked as fraudulent
Of this fraudulent traffic around 40% is from fraudulent devices, or likely spoofed devices.
This volume is not consistent across all of our clients. Not all click fraud is ad fraud.
But industries with high value CPC are often targeted by ad fraud networks, which is evident in the volume of fake traffic.
How can I spot or block fake devices on my website?
For business owners or marketers, stopping fraudulent devices from clicking on their ads or interacting with their website is more necessary than ever. With money lost on fake ad clicks climbing by billions of dollars every year, using a click fraud solution like ClickCease is the most effective, and cost effective, way to protect your site.
Although ClickCease is the industry leader in click fraud prevention, it’s now also possible to block direct or organic traffic too. So sneaky fraudsters clicking on shopping carts and processing fake payments can be called out and blocked…
If your business or website does any of these:
- Runs paid ads on Google, Facebook Ads or Bing Ads
- Has a shopping cart/checkout function
- Has a login/create account function
- Relies on it’s web presence for customers
Then spotting and blocking fake traffic online needs to be part of your strategy.
Not so sure?
Run a FREE traffic audit using ClickCease and get a unique view of your ad traffic and website visitors.
Sign up today for a free 7 day trial, pop the tracking code on your site, and start blocking fake clicks on your ads and your WordPress website.