As technology becomes more integrated into our daily lives, the risk of cyber attacks looms larger than ever before. One of the main triggers of these risks is bots and botnets. These malicious automation tools can cause chaos and destruction to businesses and their online activities.
As a result, botnet detection has become a pressing concern in the cybersecurity field. Unfortunately, many companies are not even aware of how growing this threat actually is. According to a report by Cybersecurity Ventures, “Cybercrime is predicted to cost the world $8 trillion USD in 2023”.
From small businesses to large corporations, nobody is immune to these attacks. Therefore, it’s important for the business world to enhance awareness of this topic. By adopting appropriate knowledge and measures, companies can stay alert and block botnets before they can cause damage such as data breaches, click fraud, malware, and other cyber attacks.
Understanding Botnets. How do they work?
Before we dive into the best practices for botnet detection, let’s first briefly review what bots and botnets are. We will explore how they work, what they can do, and how to deal with them.
What is a bot?
A bot, short for “robot,” is a software program that runs automated tasks on the internet. Bots can be used for various purposes, including web crawling, indexing, and automation.
However, when a bot is designed to perform harmful activities, it becomes a threat to the internet’s security. Hackers can create malicious code that mimics human behavior and do repetitive tasks. For example, they watch YouTube videos, click on ad links, or engage with social media content to boost numbers.
What is a botnet?
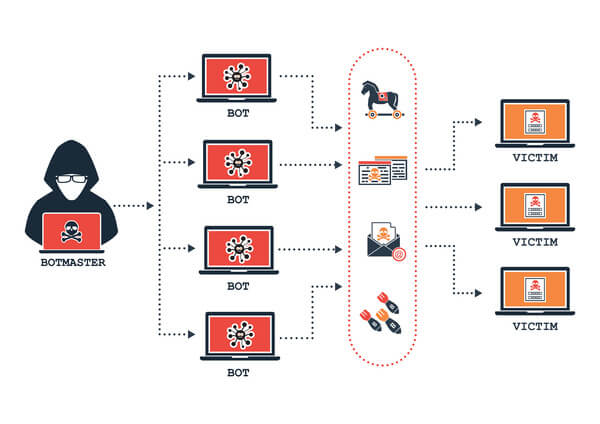
Multiple bots grouped together and working toward a single purpose form a botnet. So, basically, a botnet is a network of computers that have been infected by malware and are under the control of a single attacker or “botmaster.”
A botnet is created when malware is installed on a large number of devices, such as computers, smartphones, or any other Internet of Things (IoT) devices. These IoT devices refer to any digital device (from smartwatches to smart home devices) that can connect to the internet and share or exchange information to make our lives easier.
The infected devices are also known as “zombie devices” or “zombies”. They can be used to form a network of bots (botnet) or a “zombie army.” Each bot within the botnet can affect thousands of devices, which makes the botnet even stronger and more dangerous.
So we can imagine the kind of damage the “zombie army” can cause if not stopped in time.
How do botnets work?
Botnets work on their own until they communicate with a command and control (C&C) server. This C&C server, as well as the entire botnet, is controlled by a single person, known as a “bot herder” or “botmaster”. The botmaster commands all the bots to carry out attacks or other malicious activities. This person acts remotely, sending updates to infected machines and manipulating their actions.
Botnets may not show any malicious behavior until they are commanded to attack and the owners of the affected devices are usually unaware of this. There are two ways a botnet can be dangerous to your business.
First, it can infect one or multiple devices in your network and use it as part of a botnet. You won’t even notice that your device is used to perform malicious and fraudulent activities online.
Second, it can use its combined power to target your business. This can include distributed denial of service (DDoS) attacks, which can disrupt your operations. For example, a large number of bots can simultaneously flood a target server with traffic, overwhelming its capacity and causing it to crash. This can lead to significant downtime, loss of real traffic (and with this revenue), and damage to the business’s reputation.
Understanding how they work and their potential impact is essential in preventing and detecting botnet attacks. In the next section, we will explore the common types of botnets and how they operate.

Types of botnets and botnet attacks
Botnets come in different types, and each type is designed to carry out specific malicious activities or botnet attacks. Here are some of the most common types of botnets and their associated attacks:
- DDoS botnets: Distributed Denial of Service (DDoS) botnets are designed to conduct DDoS attacks. These attacks involve overwhelming a website, network, or servers with traffic from multiple sources, causing it to crash or become inaccessible. Cybercriminals use DDoS attacks to extort money from businesses or as a distraction while they carry out other attacks, such as data theft or malware installation.
- Click bots: Click bots are used for Click Fraud and Ad Fraud. This is a type of online fraud that involves clicking on ads to generate revenue for the attacker. Click bots can also engage with competitors’ ads or generate fake clicks. This way, advertisers are spending their advertising budget ineffectively and have inaccurate traffic statistics.
Advertisers themselves, as well as Google through its Google Ads platform, are trying different botnet detection techniques to mitigate them. However, Click Bots use advanced algorithms, which make them harder to be detected.
- Scraper bots: Used for content scraping and stealing personal information. Some botnets are designed to scrape content from websites or steal personal information, such as login credentials or credit card details. The stolen information can be used for identity theft or sold on the dark web.
- Scalper Bots: Scalper botnet attacks are designed to quickly purchase large quantities of high-demand products. The goal of the botmasters is to then resell these products for a much higher price and earn a profit. These kinds of botnet attacks are commonly used for tickets and events, major retail sales, e-commerce stores, and limited edition items.
One notable incident with scalper bots occurred not too long ago, causing “ticket chaos” for Taylor Swift’s concerts. - Spam bots: Spam bots are used to send out email spam messages or phishing emails. Phishing emails are designed to trick recipients into revealing sensitive information or downloading malware onto their devices. Spam bots can send out millions of emails in a short period, making them a powerful tool for cybercriminals.
How to prevent botnets from affecting your business
Now that we have covered the different types of botnets and their associated attacks, it’s time to focus on the most important part – how to protect your business from botnets. Botnet attacks can be very harmful, but they are preventable if you follow good security practices. Here are some ways you can protect your business from botnets:

Develop good security practices
One of the best ways to protect your business from botnet attacks is to develop good security practices. This involves securing all your devices, network infrastructure, and software against vulnerabilities. Ensure that you have a robust antivirus and firewall system in place and that you keep all your software and operating systems up-to-date with the latest security patches.
Use 2FA
Two-factor authentication (2FA) is an additional layer of security that helps prevent botnet malware from breaking into devices and accounts if a password has been compromised. By using 2FA, you will be required to enter a one-time code or confirm login attempts from a trusted device, making it difficult for hackers to gain access to your accounts.
Provide cybersecurity awareness and regular training to your users/staff
Cybersecurity awareness is essential in preventing botnet attacks. Educate your employees on how to identify phishing emails, suspicious attachments, and links. Provide regular training and reminders to your staff on cybersecurity best practices, and establish policies for safe internet usage.
Don’t open suspicious email attachments or links
Botnet malware is often distributed via email in the form of attachments or links. If you receive an email that you suspect is phishing, do not open any attachments or click on any links, even if they appear to be from a trusted source. Always scan attachments with antivirus software before opening them, or hover over the link to check the URL before clicking on it.
Regularly run ad traffic and network traffic analysis
Botnets can generate a lot of network traffic, which can indicate botnet activity. Use a network monitoring tool (Google Analytics could be useful too) to detect any unusual network activity, and regularly monitor ad traffic for any suspicious activity.
Update operating system
Botnets often target vulnerabilities in operating systems. Ensure that all your devices have the latest security updates installed. These updates often contain security patches that fix vulnerabilities that can be exploited by botnets.
By following these best practices, you can help prevent botnets from hurting your business. Keep in mind that botnet attacks can be very damaging, and it is essential to take a proactive approach to protect your business from them.
Botnet detection – practical techniques
Botnet detection is no easy feat. As we can see in this article, botmasters are constantly innovating and refining their techniques. Their main interest is to remain unnoticed, and they’re creating increasingly complex botnets to achieve that.
Despite it being a challenging task, botnet detection isn’t a mission impossible. Of course, the easiest and most effective way is to use specialized botnet detection tools. ClickCease for example can automatically block botnet attacks on your website, keeping it safe from fraudulent and invalid visits.
However, there are still some practical techniques that you can employ without the use of a tool. Several indicators can be a sign that your computer is part of a botnet or your business has been attacked by a botnet in any way.
We have categorized these indicators into three main categories, depending on the nature of the attack:
How to tell if you’re part of a botnet?
If you’ve ever wondered how to detect a botnet on your computer, these several signs can show you if it’s been infected with a bot:
- Slow computer: One sign that your computer might be part of a botnet is that it is running slowly, as the botnet could be using your system’s resources.
- Battery drain faster than usual: Botnets can consume significant resources from your device, which can cause a faster battery drain than normal usage patterns.
- Suspicious processes or programs: Check for suspicious processes or programs running on your device. For example, you can notice new apps that you haven’t installed before. If you don’t recognize them, it’d be good to investigate their origin and purpose.
- Unusual high usage of cellular data: The malware in your device can use its cellular data to communicate with the C&C servers. If you notice a sudden increase in your cellular data usage, despite not changing your usage patterns, it could indicate a botnet infection.
- Unusual system behavior: Any atypical activity on your device that deviates from its usual patterns, such as unexpected shutdowns, system crashes, or unusual error messages. These behaviors can indicate a potential botnet infection.
- Changes to browser settings: Botnets can manipulate browser settings. If you notice changes without any input from you, it could be a sign of a botnet infection.
- Unusual pop-ups: Pop-ups with ads appear on different screens and apps where you have never seen them.
- Spam emails and messages: If you receive spam emails or messages from your own or other email addresses, or if your contacts receive suspicious messages from you, it could be a sign of botnet activity. Botnet could use your device or email address to send spam or phishing messages.
Signs that your business is a target of a botnet
When it comes to the question “How to detect a botnet attack on your business?”, you can keep track of these few signs:
- Unusual time for activity: If you notice activity at unusual times, such as outside of regular business hours or during low-traffic periods like holidays, it could be a red flag that your business is under attack.
- Slow network performance: A slow network or internet connection could be a sign that your business is under a botnet attack, as the botnet could be consuming network resources.
- Unexplained data transfer: Unexplained data transfers or suspicious connections to unfamiliar IP addresses could indicate a botnet attack on your business.
- Unusual network activity: If you notice unusual network activity, such as spikes in data usage or connections to unfamiliar IP addresses, it could be another sign of botnet activity.
- Unauthorized access to systems or data: If you notice unauthorized access to your systems or data, it could mean that a botnet has compromised your business’s security.
Signs that your paid or organic campaigns are affected by a botnet
And lastly, you can notice if your paid ads or website are being affected by click fraud botnet attacks by paying attention to these signs in your analytics:
- Unusual click-through rate (CTR): If you notice that your ads are receiving significantly higher CTR than usual, it could be a sign of a click bots attack.
- High bounce rate: A high bounce rate on your website could also indicate a botnet attack, as the botnet could be visiting your website without any intention of engaging with your content.
- Low conversion rate: A botnet traffic could lead to a low conversion rate, as the botnet may not be interested in purchasing your product or service.
- Traffic spikes: Sudden spikes in traffic to your website or ad campaigns could be a sign of botnet traffic.
- Location ‘Not Set’: If your analytics show many visitors with location “Not Set”, or geo-locations you don’t target or don’t have business with it could indicate a botnet attack, as botnets often use IP addresses with fake locations.
- Repeated site visits from the same IP: Repeated visits to your website from the same IP address could mean that a botnet is targeting your ad campaigns.
- Unfamiliar useragents or old devices: Presence of unfamiliar useragents in your website analytics or a sudden increase in old devices you don’t usually see in masses could indicate a botnet attack.
- Faster spend of ad budget without engagement: Your ad budget can be exhausted at a faster rate than usual. If this is not followed with a corresponding increase in engagement with your site most likely your ads are affected by botnet clicks.
To go a step further with botnet detection efforts for your website or paid campaigns you can check out ClickCease. It will automate this process, providing comprehensive and full protection. By blocking malicious clicks from your ad campaigns, or any other form of fake traffic on your WordPress site, you can ensure that you’re spending your budgets and time on real, human traffic only.
So if you want to have a clear picture of your marketing efforts and take your botnet detection strategy to the next level, try ClickCease with the free trial.
FAQs
What is a botnet?
A botnet is a network of computers that have been infected by malware (bot) and are controlled by a single attacker or “botmaster.” Each infected device, known as a “zombie” is part of a “zombie army” and works toward a single malicious purpose.
What are some botnet detection methods?
The most effective way to detect and block botnets is through the use of botnet detection tools like ClickCease. Some manual methods that you could use without a tool involve regular monitoring of your device and network activity to detect unusual patterns. This can include tracking network traffic, examining system logs for signs of suspicious activity, or tracking user behavior to identify anomalies.
How to detect a botnet on your computer?
A few signs can show that your computer or network has been infected with a bot:
– Slow computer
– Battery drain faster than usual
– Suspicious processes or programs
– Unusual high usage of cellular data
– Unusual system behavior
– Changes to browser settings
– Unusual pop-ups
– Spam emails and messages
How to detect a botnet attack on your business or campaigns?
There are several indicators in your network or traffic analytics that your business has been targeted by a botnet attack:
– Unusual time for activity
– Slow network performance
– Unexplained data transfer
– Unusual network activity
– Unusual click-through rate (CTR)
– High bounce rate
– Low conversion rate
– Traffic spikes
– Location ‘Not Set’
– Repeated site visits from the same IP
