Cyber attacks have become more sophisticated, with hackers finding increasingly clever ways to steal data and access websites and databases. One of the main ways that a hacker will access a website is by using a brute force login or brute force attack.
A brute force attack refers to an attacker submitting multiple passwords in hopes of guessing the correct combination to gain unauthorized access to your systems. The software used by the hacker can often secure entry to a website, email account, or other database in seconds.
It’s called brute force because the attempts are performed vigorously and continuously until the username and password are secured. Brute force attacks are simple but highly effective means of cracking your encryption keys and accessing files you want to keep secret.
How do brute force attacks work?
On a basic level, brute-force logins are as simple as guessing possible passwords. But the key is to try multiple variations until you arrive at the answer.
The longer the possible passwords, the more variations you’ll have to try. A 2 digit passcode has 100 possibilities, while a five-digit passcode has 10 billion. Also, think about the fact that most passcodes aren’t just digits. They contain alphabets, capitalization, and special characters. This is why weak passwords are easier to guess than complex passwords.
If you’ve ever wondered why websites insist you use complex passwords, this image may help explain.
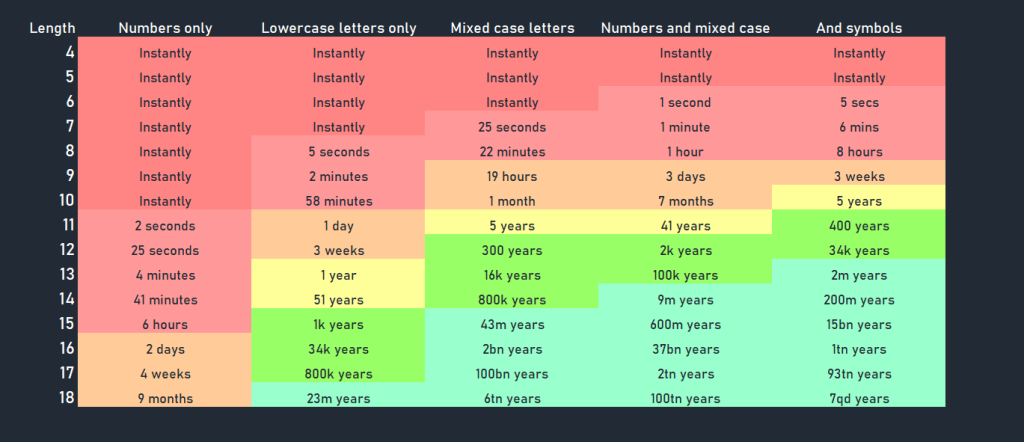
As you can see, simple passwords can be cracked using brute force attacks in less than a second. But the more complex they are, the longer they take to compromise.
So one of the main ways of avoiding brute force attacks on your website is to require all users to have long and complex passwords. In fact, password security is now seen as the first line of defense against many forms of cyber attacks.
Another issue is that due to the massive computing power required, using a brute force bot can raise computing speed and simplify access to your systems.
Why aren’t brute-force attempts flagged?
There are multiple ways that hackers avoid detection during an attempted brute-force login.
1. They use multiple IPs
If you have too many failed login attempts as a result of entering the wrong password, most systems will ask you to wait a while and try again or lock you out completely. So why don’t these hackers suffer the same fate?
Brute force login attempts are executed in a cunning and systematic way that involves multiple computers and IP addresses.
One tactic used is called a distributed attack, where each IP only attempts to guess your password a limited number of times, after which it stops completely. Another IP then takes its place.
Now, multiply this on a large scale, with dozens or even hundreds of bots trying to log in all at once but never trying enough times to trigger a safety mechanism.
2. They aren’t just guessing
During brute-forcing attacks, the hacker acts based on some available information. For example, most people use the same password on many platforms, so a data breach from another platform is a pretty good starting point. This is known as a reverse brute force attack because a hacker tries multiple usernames until they find one that fits the password.
There are also other tactics. For example, hackers may use dictionary attacks where the hacker runs through passwords using standard words – for example, ‘password’, ‘admin’, ‘iloveyou’, or ‘1234567890’.
A dictionary attack is a common method of breaking down simple passwords and one that is alarmingly successful and used often. Hackers may also use hybrid brute force attacks that combine dictionary attacks with basic brute force attacks.
Famous examples of brute force attacks
Alibaba (2015)
One famous brute force attack example is Alibaba’s Taobao site. Between October and November of 2015, the e-commerce giant suffered a brute force attack that went undetected by the security team. In this case, the excessive login attempts weren’t flagged because of Taobao’s consistent high traffic.
Reports claim that reused passwords were responsible for some of the compromised accounts as the hackers reused stolen account credentials from other sites. The hackers had over 99 million account credentials to work with, and they successfully hacked over 20 million user account profiles.
Club Nintendo (2013)
Club Nintendo is a community membership site where users discuss all things Nintendo. In 2013, the site suffered a brute force attack, where, after 15 million attempts, hackers finally cracked user accounts.
Thankfully, all the compromised accounts were quickly suspended until they could be returned to the rightful owners. Reports suggest that the attack affected over 25,000 forum members.
GitHub (2013)
GitHub is arguably the biggest brute force attack example in history. In 2013, hacks obtained access to multiple user accounts after several attempts from nearly 40,000 unique IP addresses. Reports suggest that the hackers used information obtained from other data leaks.
GitHub stores user passwords securely, and even though it’s unclear how many accounts were compromised, estimates show that they were very few.
What’s the goal of a brute force attack?
User data is incredibly valuable in our digital world. From payment information or tax details to simply accessing email addresses and passwords. These are the main reasons for brute force attacks.

Access to your user data
Websites with a lot of user data are often targets for brute-force attacks. Once successful, hackers can not only gain access to the user account but can often use these login details on other websites too.
In fact, with a database of known user details, hackers can carry out brute-force attacks using these harvested details on websites across the internet.
Exploit web resources
With specific hacks like a brute force WordPress login, the attacker seeks to use your website’s resources to their advantage. For example, they may want to use your website to send spam and phishing emails without your knowledge. Hackers may also use your site to hack other sites because your IP is probably not blacklisted just yet.
Other reasons to brute force WordPress login include mining cryptocurrency or redirecting your site’s traffic.
Explore vulnerabilities
White-hat hackers, often referred to as ethical hackers or hacktivists, don’t have any malicious intent. Instead, they test the strength of a system’s security to weed out vulnerabilities and report them. Thus, a white-hat hacker may carry out a brute-force attack on websites as a part of a security check.
How do you prevent a brute-force attack?
Like most elements of cyber security, preventing brute-force attacks can be done with a number of simple steps.
Use complex passwords
8 out of 10 confirmed data breaches are due to weak or stolen passwords – the aforementioned dictionary attacks. So a great place to start is to ensure that your passwords are:
- Strong (a combination of letters, numbers, and special characters)
- Unique across all platforms
- More than 12 characters
Automated brute force attacks using common passwords can enter a website or user account in seconds.
Limit logins to specific IP addresses
Restricting certain IP addresses from accessing your site can also discourage brute-force attacks. Many security databases have records of brute force bot IP addresses. By blocking these IP addresses, hackers need to work extra hard to access your website successfully.
One way to do this is to set up a remote access port to a static IP address. You could also configure a VPN.
Use two-factor authentication
Two-factor authentication is often considered the first line of defense against brute-force attacks. They ensure that hackers can’t gain access to your data with just a username and password. They would need your smartphone or email client as well.
Monitor your server logs
Keeping a close eye on your server logs is a more proactive way to protect your website from brute-force attacks. Logs record every failed login attempt, and by analyzing them, you can identify suspicious activity.
Use tools like Logwatch to perform daily checks and generate reports you can easily interpret.
Prevent bot activity on your site
Because automated bots usually carry out brute force attacks, blocking this form of traffic is one of the most effective ways of avoiding them.
Bot Zapping from ClickCease blocks bot traffic on WordPress websites. This means that cyber-attacks such as SEO spam, DDoS attacks, and brute force attacks are prevented proactively and in real-time.
If you run a site with a user database, a checkout function, or even if you manage a high-traffic site, you need to consider blocking bot traffic as an essential security feature.
Beyond the brute force attack
Although a brute force attack can be damaging for a number of reasons, the threats to your online business are many and varied. And, as mentioned above, it often comes down to bots.
Bad bots drive the majority of malicious and damaging activity on the internet. So taking care of network security and preventing bots of any sort from gaining access to your website means you can be protected from the following:
- Data breaches and the ensuing damage to your reputation
- Damage to your website infrastructure, such as malware installation or content injection
- Website taken offline in DDoS or ransomware attacks
- Click fraud and ad fraud damaging your paid ad campaigns
Bot Zapping from ClickCease is a new product as part of our anti-fraud toolkit for marketers. Currently, it works only for WordPress websites, although WordPress sites account for 40% of the internet.
Existing ClickCease users can run a free month of Bot Zapping to see how it works.
New users can sign up for a free trial to run a site traffic audit.
